$1 Million is Just the Beginning: Q4 2020 in Network Access Sales
Victoria Kivilevich, Threat Intelligence AnalystMultiple initial network accesses continue to appear for sale in underground forums every day, partially becoming an initial entry point for ransomware operators. Following KELA’s analysis of initial access brokers’ activities in September 2020, we’ve assessed the listings of network access from all of Q4 2020.
We’ve shared some of the major takeaways below:
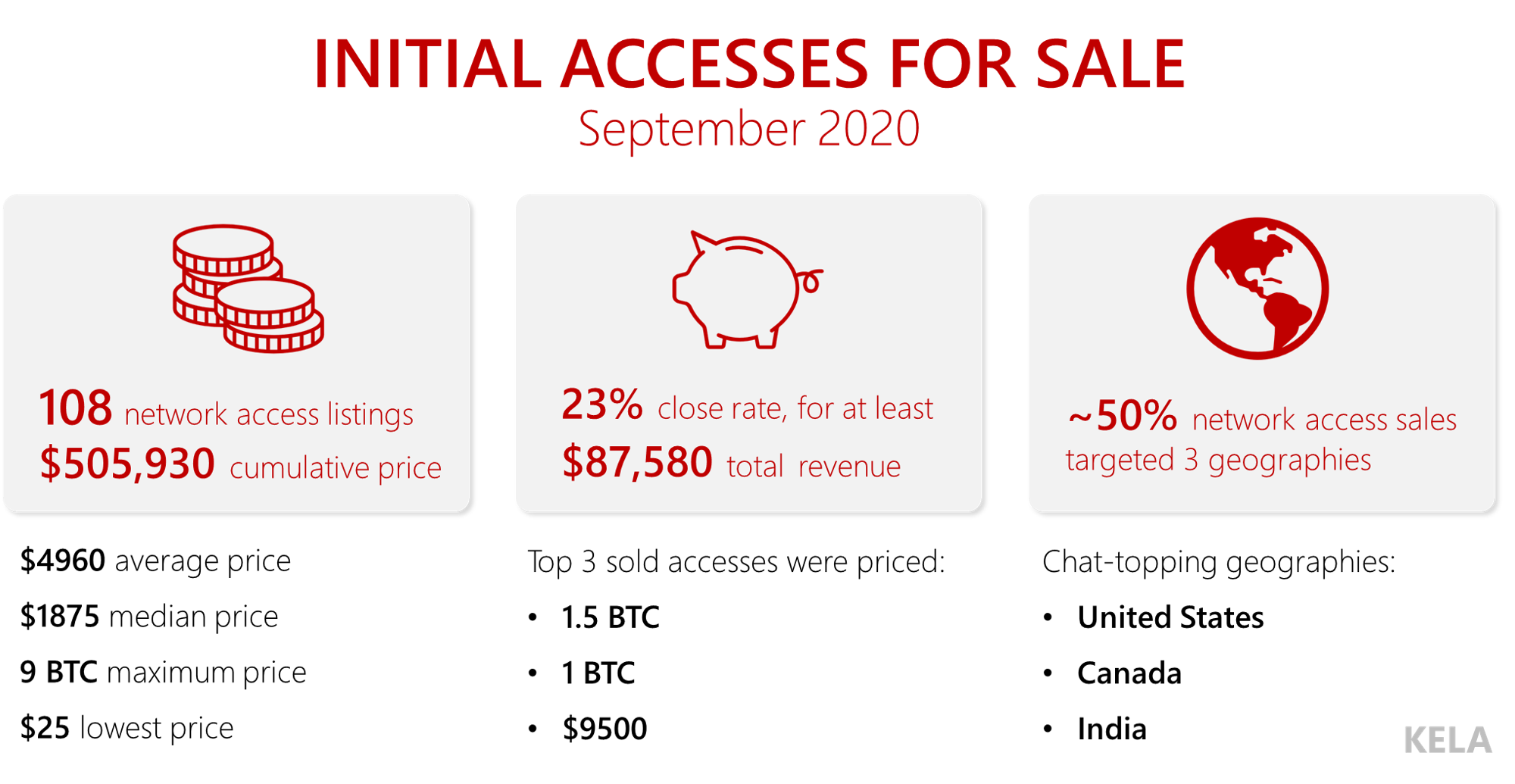
KELA traced almost 250 initial network accesses listed for sale in Q4 2020. The cumulative price requested for all accesses surpasses $1.2 million. On average, we observed around 80 accesses offered for sale in each month of Q4 2020.
Out of these network access listings, KELA found that at least 14% were noted as sold by actors.
As the overall month-to-month number is lower than in September (108 accesses), KELA identified a growing trend of accesses being sold in private conversations rather than publicly in forums, likely the cause for the slight decline.
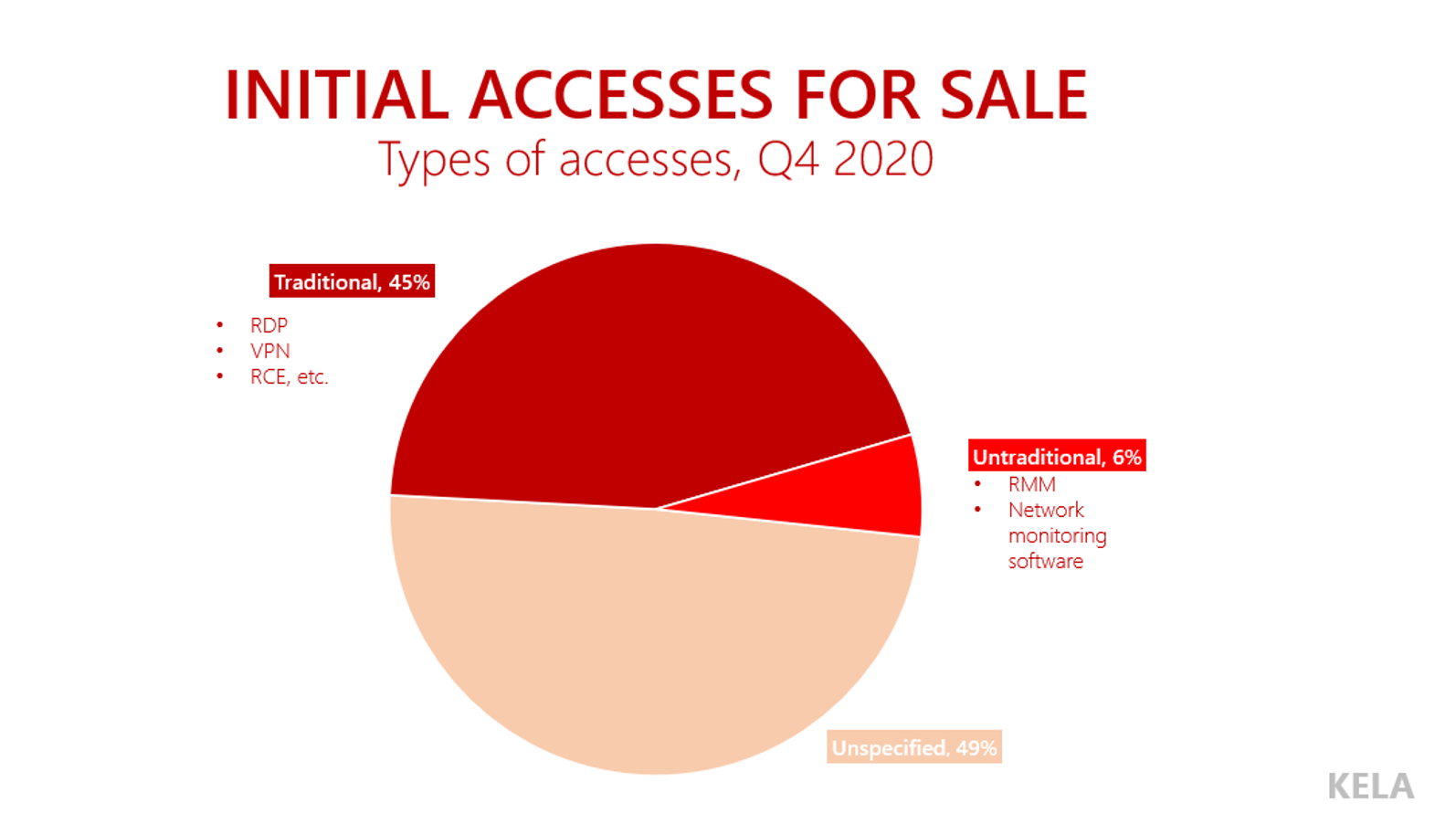
While establishing a list of the most expensive accesses and the TTPs of their sellers, KELA discovered that the attack surface is constantly expanding, with initial access brokers offering new access types. Meanwhile, RDP- and VPN-based accesses, as well as vulnerabilities (allowing to run code using a specific flaw and potentially enabling actors to pivot further within the targeted environment), constitute the majority of the offers.